The short answer is that yes there are ports that you’ll want to block outbound by default. There’s a variety of amplification attacks that you have the possibility of being a member of. These attacks aren’t against your systems, but you run the risk of your machines being used to amplify attacks against others. These could be DNS based, NTP Based, or other kinds of amplification accounts.
Occasionally I get notifications from Azure that they see these ports open, and that you should network Network Security Groups to closed the unneeded ports.
Two of the ports that I’ve needed to deal with recently are UDP 123 and 389. Blocking these was a minor issue but best practice.
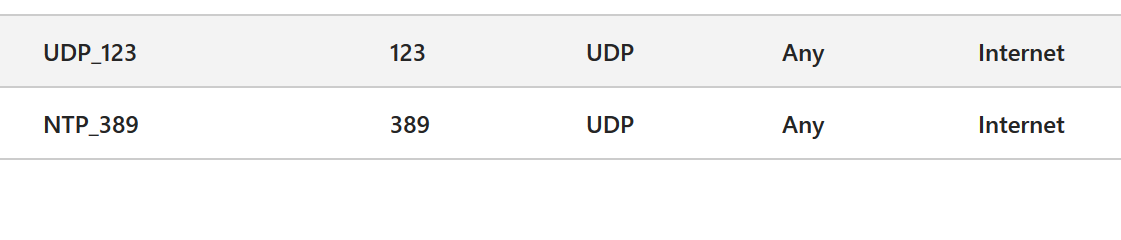 Blocking these in Azure is super low risk and easy to implement,
Blocking these in Azure is super low risk and easy to implement,
To be clear there is no inherent risk of being in Azure compared to other platforms. These sorts of amplification issues can come up in any environment. The beautiful thing about Azure is that they monitor these outbound issues and report back to the end on what blocking needs to be done for successful implementations,
Denny
The post Should I be blocking outbound ports in Azure by default? appeared first on SQL Server with Mr. Denny.
