When setting up linked servers, what security settings do you typically setup for that question at the bottom of the window?
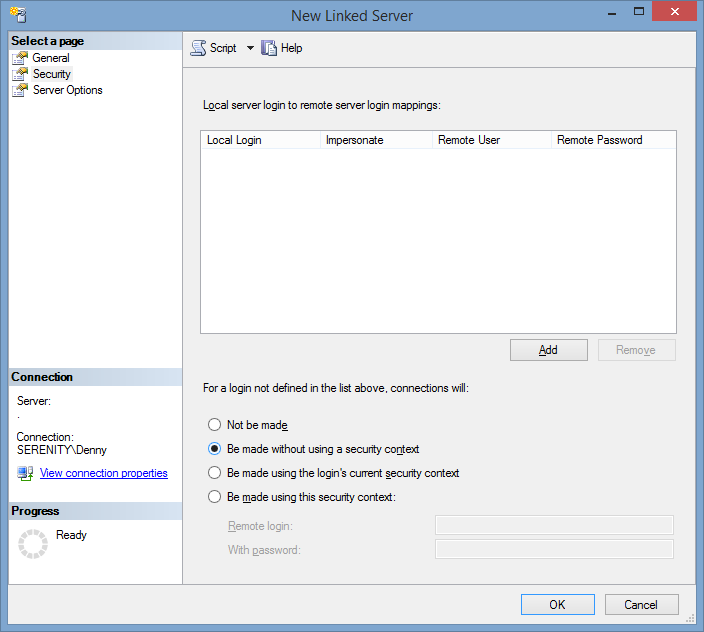
As you can see from the screenshot there are four options. Two of them are good options, two of them are bad options. Do you know which ones are which?
The Bad Options
The two bad options to choose are the second (Be made without using a security context) and fourth options (Be made using this security context). These both have different problems, but for the most part they are just bad.
When you select the without a security context the SQL Server attempts to connect to the remote database using anonymous authentication. If the remote server is setup to allow anonymous authentication then the user is able to log into that system and run queries against the remote database, possibly even dropping objects or changing data that shouldn’t be changed. All without any possible auditing on the remote machine.
When you select using this security context anyone who comes into the SQL Server can access the remote server using whatever account is specified. So if the account which you list has admin rights then everyone on your SQL Server has admin rights on the remote server, which is bad.
The Good Options
The much better options are to use the first option (Not be made) or the third option (Be made using the login’s current security context). These are much more secure because they either don’t allow access through the linked server, or they require that the users login has access to the remote server. Either way, these are much more secure options than the two listed above.
Now there are cases when you need to use one of the two options listed above as the bad options. For example if you need to access a Microsoft Access database, or an Excel sheet, etc. But these are the exception not the rule.
Denny
