What if I told you just using multi-factor authentication (MFA) wasn’t enough anymore? The Lapsus$ hacking group, who were at least partially made up of a group of teenagers in the UK, took a very targeted hacking approach. They used password stuffing to try to breach the password credentials of power users within organizations they were targeting.
Once they identified the passwords (through a variety of tactics, but mostly password reuse—use a god damned password manager) , they sent 100s of MFA requests to multiple users. While a single user may have the discipline to ignore a series of MFA approvals that they didn’t prompt themselves, the odds are that if you send them to several people many times. Once that happens, and the attackers have an admin token, they can then move laterally, secure command and control, and do all manner of other bad things around credentials.
If this sounds scary, and it does to me, who is by far not an expert in all things security, but knows a little bit, you may ask, what are some alternative solutions? The answer to that question is Fido2, a different protocol for MFA and auth. Remember all of that stuff Microsoft talks about with passwordless login? That’s all based around Fido2. I configured this for DCAC’s Azure Active Directory yesterday, and I wanted to walk you through the steps.
Step 0 is to acquire a FIDO2 key for you and/or your team—I have a Yubico 5c, but there are others you can consider.
After that, the first step was to go to the Azure Portal and navigate to Azure Active Directory authentication methods.
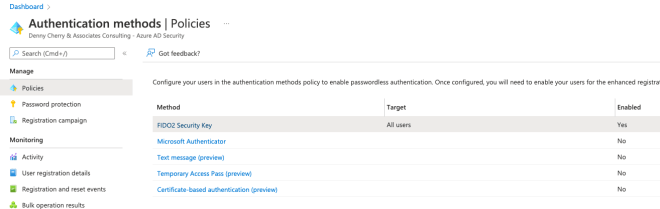
Click on FIDO2 security key–even though it shows as enabled here, it is not enabled by default. When you click on the text you will see the next screen.

In this case, I enabled for All Users–this doesn’t mean they have to authenticate using this method, just that they have the option to. You also have some advanced options that go above my pay grade and are not happening in DCAC’s AAD.
Following this–I configured my Macbook to use my Yubi key as a authentication method. I followed the guidance on their site here. After doing that configuration, I was ready to make the change to my account. Navigate to myaccount.microsoft.com and select Update Info, under security info.

Once there, you can add a method, which is called “security key” here. I think this can be done globally in your org, but for this basic trial, I just enabled it for myself.

So that’s all of the prework you need to do. Now–let’s show logging into the Azure portal. You have to change the options in the portal as shown below:

Once you have selected Sign in with security key, you will prompted to choose the key. I was also promoted to touch the key (not captured in this screenshot) and then to enter the PIN you created when configuring your key.

Once you have entered your PIN, you are now authenticated to the Azure portal, without using a password. What I would love to see, but haven’t been able to configure is the ability to set a conditional access policy for AAD where untrusted location logins were required to use a harder level of authentication like a security.
